How to Avoid Email SPAM
 |
Email is one of the oldest forms of digital communication, and forms the basis of many commercial transactions. In the past dozen years, however, email SPAM, much like "junk mail", has become the bane of our existence these days. It's gotten so bad that it's almost mandatory for email providers to provide SPAM filters. But the big question is how did they get my email address in the first place? This articles explores how email addresses are commonly acquired and what you can do to prevent this. |
How Did They Get My Email Address?
One question you might ask is how did they get my email address? Unfortunately there are many avenues by which attackers can collect email addresses. The most common ways that attackers gather email addresses include harvesters, mailing lists and dodgy websites.
Harvesters
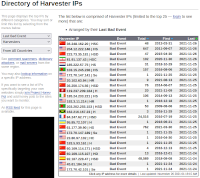 Harvesters
are automated systems that crawl through the worldwide web looking
for emails. In a certain sense they act very much like search
engines in that they scan websites for content. The
difference is that their focus is strictly on looking for email
addresses left exposed. Project Honey Pot
has done a great job in monitoring these systems. However
please bear in mind that blocking IP addresses from accessing your
website is probably an exercise in futility as the attackers can
easily disguise their actual IP address by using VPNs, or just
forging packets. Also, if the attacker has control over a
botnet,
you might see tens of thousands of unique IP addresses, making it
impossible to effectively block.
Harvesters
are automated systems that crawl through the worldwide web looking
for emails. In a certain sense they act very much like search
engines in that they scan websites for content. The
difference is that their focus is strictly on looking for email
addresses left exposed. Project Honey Pot
has done a great job in monitoring these systems. However
please bear in mind that blocking IP addresses from accessing your
website is probably an exercise in futility as the attackers can
easily disguise their actual IP address by using VPNs, or just
forging packets. Also, if the attacker has control over a
botnet,
you might see tens of thousands of unique IP addresses, making it
impossible to effectively block.
The image shown here is taken from the Harvesters menu
option on the Project Honeypot website. Here is the link to
visit this page: https://www.projecthoneypot.org/list_of_ips.php?t=h.
Let's now have a look at another way attackers can get your email
address: from a mailing list.
Mailing List for Sale
Even the most supposedly security and privacy conscious organizations will sell their email list to the highest bidder. Most notorious are banks and other financial institutions. Also, what do you think Google and Facebook are doing with your private information? If you think that information is not being sold, dissected, and analyzed right now you are definitely living in a bubble!
One way to protect yourself from the institutional sale of email addresses is to create an email address alias. Most email providers and web hosting providers give you a certain number of additional email accounts. Others will also throw in email forwarding for free. The way this works is that you create an email address that simply forwards into your real email account. It's a great way to track who's selling your information. Also, if the SPAM generated from the email forward gets to be too much, you can simply delete the forward without any harm done to your primary email account.
Some years ago I signed up with Equifax (yes ... that Equifax, the one that got hacked!). I provided an email forward when they asked for my email account upon registration. I then, very specifically, indicated in my email preferences that I did not want to receive any of their marketing emails. Within 2 months I found myself bombarded with marketing emails from a bewildering number of firms I'd never heard of before. Checking the recipient email address quickly confirmed that my email address had been sold by Equifax. When I confronted them over this they swore up and down that they would never sell my email address or other account information. I then pointed out to them that the only organization that was aware of the fake email address I'd given them was Equifax. And, of course, they still denied doing so. I then promptly cancelled my account. How can I trust them to keep my credit information secure when they couldn't even secure a simple email address? A year later my decision was vindicated with the famous Equifax hack that compromised hundreds of millions of customers.
Let's now have a look at another way attackers acquire email addresses: through dodge websites.
Signing Up on Dodgy Websites
In many cases you might have inadvertently signed up for an account on a dodgy website. The website owner then turns around and sells his or her email list to the highest bidder. Porn websites and fake bitcoin exchange websites are notorious for this. One example is the Yuan Pay Group pictured here:
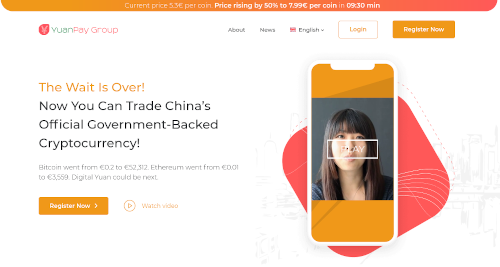
This website looks quite modern and professional. Also, the premise is quite brilliant and somewhat based on reality. The premise is that the Chinese government is developing its own government-backed crypto currency. If you continue reading on this website they'll tell you they are the "exclusive agents" to sell this currency, authorized by the Chinese government, which, of course, is not at all true.
In reality it's just a facade for a group of attackers who are only interested in stealing money from you! If you click on Register Now you're taken to a form where you fill in your name, phone number and email address. You are then automatically redirected to a random even-dodgier website that claims to be a crypto currency broker. The one I was redirected to was based in Belarus, which, in itself, raised red flags. If you actually did supply your name, email address and phone number (which I actually did, much to my embarrassment!), what follows is a never-ending series of SPAM emails (with other phishing attacks), as well as phone calls.
Warning: DO NOT go to this website!!! The link is not included. For more information on this scam see this article: Yuan Pay Group Review, Scam Trading App?
Let's now turn our attention towards ways to obscure your email address.
Ways to Protect Your Email Address
As we mentioned in the section above entitles Mailing List for Sale, a great way to protect your primary email address is to create an alias. In the case where you own a business and need to display your email address on your website, however, this technique does not prevent harvesters from acquiring the alias. You're then back to square one because the SPAMmers will simply start bombarding your alias email address with junk email. You can't simply divert email going to this address to a junk folder because you might have legitimate customer requests buried in the mountain of SPAM. Accordingly, you'll need another way to display a valid email address so your customers can contact you, while at the same time preventing the email address from getting harvested. This techinique is known as obscuring your email address.
One easy way to obscure your email address on your website is to not show your email address at all. Since you still need a way for customers to easily get in touch with you, a simple email contact form is a good solution. Most CMS packages offer an email contact form, module or extension. One example is our own Simple Email Contact Form written for Joomla. You can see it on this page. If you are creating your own email contact form, don't forget to include a unique token to validate your form. It's also a good idea to include a CAPTCHA to prevent SPAMmers from bombarding you with emails by using your own form against you. An example of a PHP contact form that uses a unique token and also a CAPTCHA can be seen here.
Obscuring your email address is not that difficult, but please bear in mind that harvesters have become much more sophisticated over the years, and can read email addresses that are badly obscured. Let's have a look at a few techniques to obscure your email address.
Obscure Your Email Address Using HTML Entities
An HTML entity is a special HTML code that you can insert into your HTML web page that causes your browser to display the desired character. At the same time, that character is not directly visible to harvesters as they are reading the direct HTML source, not the final output. A comprehensive list of all currently supported HTML entities can be found at the dev.w3.org website.
One character all harvesters look for is the "at" symbol ("@"). Your immediate thought might be to render your email address as follows:
email@company.com
It will appear on your website like this: email@company.com. However, most harvesters will immediately "see through" this trick and still harvest your email address! A better approach, following the same line of thought, would be to use Greek (or other) characters that resemble English lettering. So, you might try something like this:
email@company&period𝕔𝕠𝕞
which then appears on your website like this: email@company.𝕔𝕠𝕞
Obscuring Email Using JavaScript
Another popular approach is to render your email address using JavaScript. It gets a bit tricky, however, as JavaScript deals with Unicode and not simple ASCII codes.
Here's an example of a JavaScript code block that could do that:
<script language="javascript"> addr =[101,109,97,105,108,64,99,111,109,112,97,110,121,46,99,111,109]; for (i = 0; i < addr.length; i++) document.write(String.fromCharCode(addr[i])); </script>
The final result would be:
Using PHP to Obscure an Email Address
If PHP is available on your sever, you can do the same thing as with the JavaScript code using a code block such as this:
<?php $addr = [101,109,97,105,108,64,99,111,109,112,97,110,121,46,99,111,109]; foreach ($addr as $code) echo chr($code); ?>The final result is this:
email@company.com
Obscuring Your Email Address Using Graphics
Probably the best possible technique is to simply display your email address as a graphic. Do a screenshot of your email address, trim it down, and display it on your website using the HTML image tag. This is a great technique, and puts it beyond the reach of all but the most sophisticated harvesters, those with OCR (Optical Character Recognition) capabilities.
If you insert an image tag that might appear like this:
<img src="/images/avoid_email_spam_using_graphics.png" />
It would then appear on your website like this:
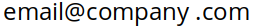
That wraps up this article. Here are are some final thoughts
Resources
Here are a few great articles on obscuring email addresses:- Excellent overall article on email obfuscation:
Anti-spam measure: Against bots harvesting email addresses - Good study on harvesters, although it's a bit dated (2011):
Longtime Behavior of Harvesting Spam Bots - Article on creating anonymous email accounts: How to Create an Anonymous Email Account
- Tech Radar has a pretty informative article here, but there's lots of ads: How to make your email more secure
Final Thoughts
 There
is a marked tendency in the media, especially the US media, to
apply nationalistic profiles to attackers. You always hear stories
about Chinese, North Korean or Russian hackers. It's
always going to be somebody else if you trust the
mainstream media. The truth, however, is that most likely the
invasion of privacy originates from supposedly trusted
actors. For most of us, the attackers are probably any of a
number of spying organizations run by our own government.
Another primary source are supposedly trustworthy
organizations. But we've all heard enough stories by now that
we know that the tech giants do not have our best interests in
mind.
There
is a marked tendency in the media, especially the US media, to
apply nationalistic profiles to attackers. You always hear stories
about Chinese, North Korean or Russian hackers. It's
always going to be somebody else if you trust the
mainstream media. The truth, however, is that most likely the
invasion of privacy originates from supposedly trusted
actors. For most of us, the attackers are probably any of a
number of spying organizations run by our own government.
Another primary source are supposedly trustworthy
organizations. But we've all heard enough stories by now that
we know that the tech giants do not have our best interests in
mind.
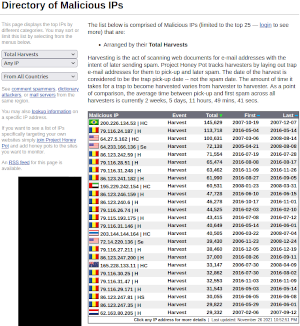
Hard statistics seem to bear this out. As an example, an American might assume that most harvesters are based in whatever country is the current bogyman. However, if you look at the origin of the worst overall harvesters (shown in the image), you can see that two American IP addresses appear in the top 10. The other IP addresses originate from countries that you would not normally associate with hackers or SPAMmers.
The image shown at the left summarizes total harvests by IP address. You can get the current list from Project Honey Pot by clicking here. Bear in mind, however, that the harvesters could be using a VPN or other device to obscure their IP address, so these statistics might be misleading.