 |
How to Spot Email Phishing24 Jan 2022 Unfortunately, email phishing, one of the earliest means whereby an attacker gains unauthorized access to your system, is still very much alive and well. Numerous articles have been written on the subject. In this article real-life examples are presented in an effort to help you to detect and avoid email phishing attacks. |
As you read through this article, please bear in mind that any one of the suggestions given here by itself might not be "bullet proof". However, the combination of suggestions will hopefully prove helpful in identifying SPAM emails that might form the basis of a phishing attack. In this article we won't define phishing attacks, as they have already been very clearly discussed and defined over the years. If you are unclear on what exactly is a phishing attack, please run this search to get a list of current articles on the subject: https://duckduckgo.com/?q=phishing+attack&t=h_&ia=web.
Email Phishing Cheat Sheet
Please note that a number of these suggestions are specific to English language speakers. However, for sake of the billions of people on the planet who are fortunate enough not to speak English, many of these suggestions still apply. (Aside: I realize that the latter supposition is paradoxical, but will ignore that for the time being!)
Here is a brief summary of ways you can identify am email phishing attack.
| Suspicious Recipient Email Address | If the direct recipient is not you, and you're on the CC or BCC list, be wary unless you know the sender. |
| Suspicious Recipient Name | If the recipient's name isn't your proper name, there's a good chance the name was "derived" algorithmically. |
| Suspicious Sender Email Address | If the email address of the sender doesn't match the domain name of who the message says it's from, it's most likely SPAM. |
| Spelling Errors | If the email is from a person, spelling errors might be expected. However, if the email claims it's from a bona fide company, most corporations have spell checking enabled on their email systems and do not allow company email to be sent out with spelling errors (unless the company employee is extremely careless). |
| Grammar Errors | The same logic applies to grammar errors as it does to spelling errors (see above). |
| Direct Links to Click | Most legitimate companies do not send emails with direct links, although there are quite a few exceptions, unfortunately. Most companies instruct you to first login to your account, and then do X, Y or Z. Also, hover over the link with your mouse and confirm that the website in the link matches the website mentioned in the email. |
| Urgent Action Requested | Whenever an email tells you that you need to take Immediate Action, or that some requires your Urgent Attention, be very suspicious. Most legitimate companies will give you plenty of advance warning whenever something requires your attention, and instruct you to login to their website and check for alerts and notices. |
| Threats | In many cases, the SPAM email will issue a dire warning with a threat along the lines of your access will be terminated unless ..., or your account will be suspended unless .... In other variations, SPAMmers will say something like suspicious activity was noted on your account... |
| Asking You to Enter Credentials | If you receive an email with a direct link to click, and you're prompted to enter your login name, password, PIN code or other identifying credentials, be immediately suspicious. If in doubt, open a new browser tab and login to your account and check for warning, alerts or notices. If still in doubt, contact tech support or the help desk for that company. |
Now that you've got the general idea of what to look for, let's have a look at a few actual examples that I've received over the years.
It Looks Official, But ...
Here's a prime phishing example that conveniently arrived in my inbox just this morning:
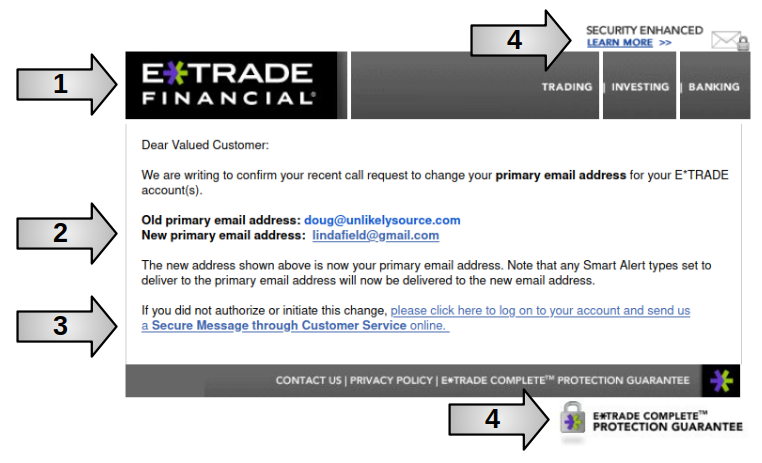
Here are some things to note:
| 1 | Official Logo | Most attackers will rip graphics off the official page, and put together something that looks official. |
| 2 | Common Sense | Why on earth would eTrade change my email address? How are they going to communicate with me, assuming this were true? Also, why pick this extremely odd address at random out of thin air. This makes no sense at all. |
| 3 | Website Mismatch | When I hovered my mouse over these links, the website that shows up in the bottom left corner of my browser does not match eTrade at all. |
| 4 | Security Stickers | At the top right and bottom right you can see reassuring security stickers. Attackers will often do this to put your mind at ease. |
The most obvious thing to note, however, is that I have no eTrade account! If you get an email supposedly from a company with which you have no relationship, it has to be an email phishing attack. The attackers "cast the net widely" and see if they can catch any unwary fish!
Quick 'n Dirty
Sometimes the email phishing attacks are short and to-the-point. Wham bam thank you ma'am as David Bowie once lyricized. Here is an example from that category received just today:
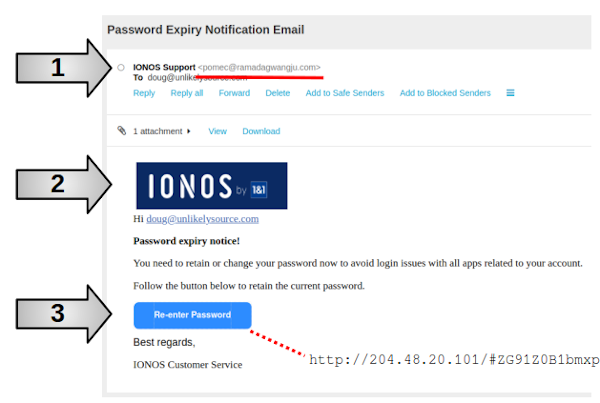
Here are some things to note:
| 1 | Bad Email | The from email address has no bearing on Ionos. There's absolutely no reason why a representative from Inonos would send an official email that not from the company domain. |
| 2 | Looks Official | THe attackers have duplicated the Ionos label just to make this look "official". |
| 3 | Bad Link | Here I added a dotted line and show you the actual URL you are sent to if you push this button. This is visible by simply hovering your mouse over the button (but DO NOT click on it!). |
Another thing to note is the warning message. The attackers obviously assume that I'm viewing this email from a mobile phone. Otherwise the reference to all apps would make no sense. However, in fact because my mobile phone is Android based, the primary email address is from Google. In other words, this email really makes no sense whatsoever.